This is second session in the series of posts on Cryptography. I would recommend you to read the previous article on the same before you go through this article. It will help you build your better understandings on Cryptography & Cryptosystem.
Revision from previous session:
We have learnt below topics on Cryptography:
- Origin of Cryptography
- Evolution of Modern Cryptography
- Secret Key
- Definition of Cryptography
- Cryptanalysis
- Objectives of Cryptography
Session 1 Link- Cryptography: Basic Understanding
Let us begin second session today.
What is Cryptosystem?
Cryptosystem is the infrastructure or environment to implement the cryptographic techniques. It provides important information security services.
It is also called as Cipher System.
Cryptosystem takes sole responsibility to deliver the message to the authorized receiver only. It protects information from any leakage by protecting with encrypted codes.
If you are familiar with the basic of communication system (In electronics – Analog & Digital) then it will be very easier for you to understand complete set up of cryptosystem. But for those who are unfamiliar with communication systems still you do not need to worry because I am your mentor so I am going to teach you.
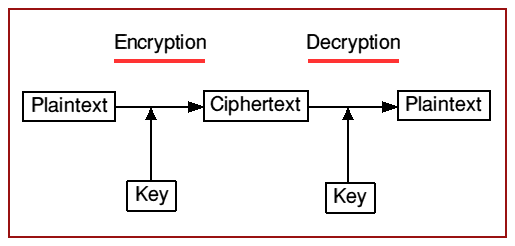
How Cryptosystem works?
There are two terminals, one is Sender end and another one is Receiver end.
Step 1-
At sender’s end, Encryption system generates Cipher text as output on getting message (plain text) and encryption key as input.
Step 2-
At receiver’s end, Decryption system gets Cipher text as input from sender’s terminal and it gets mixed with Decryption key. After further processing authorized user at this terminal receives the original message sent by sender.
You must know Encryption system and Decryption system is basically the respective algorithm. It only works when it combine together with respective keys. Authorized user is know to Encryption key and Decryption key .
In whole process there is a chance of attack on the cipher text. Cipher text might get leaked by Interceptor. He may get Encryption algorithm as well as Decryption algorithm, However he must be knowing Encryption and decryption key to read the message.
Types of Cryptosystem
There are mainly two types of Cryptosystem, which are listed and elaborated as below:
- Symmetric key encryption
- Asymmetric key encryption
Let us discuss each one of them in details.
Symmetric key encryption
In this process of cryptosystem, both sender and receiver use the same key for the encryption as well as decryption of the cipher text.
This system is also referred as Symmetric key cryptosystem and Symmetric cryptographic.
Examples: BLOWFISH, Triple-DES, Digital Encryption Standard (DES) and IDEA.
Symmetric key encryption system is highly used because of certain importance in Cryptography since early years . Each sender and receiver has to establish a secret symmetry key before any communication with this system. Apart from this, if receiver loses the key to any interceptor then he must prior inform this incident to sender to avoid leakage of plain text.
Features
- Keys can be changed regularly prior to send any information
- Very secure infrastructure
- It allows to share information in a group of receptors
- Faster exchange of information
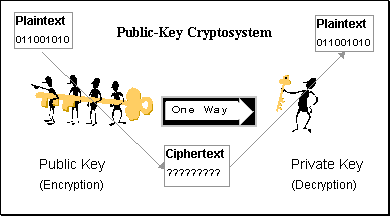
Asymmetric key encryption
In this process of Cryptosystem, both sender and receiver use the different key for the encryption and decryption of the information.
Concept of Public key and Private key comes into picture for Encryption and Decryption of the information.
Example:
There are two hosts, Host 1 and Host 2. At sender’s terminal, if host 1 wants to send information to host 2, then Host 1 will use Public key of Host 2 to encrypt the plain text. At receiver’s terminal, host 2 will decrypt the cipher text by using its own Private key.
Public and Private keys are in mathematically coded relationship to establish the correlation between both of them.
Here there are lot more chances to have malicious codes in public key. So to avoid this issue we may ask third party for security through digital signature in public key.
Features:
- Highly secure
- Less chances of interceptor attack