We have learned traditional cipher techniques and various core cryptographic techniques so far. Let’s move forward and discuss on Block cipher and Feistel block cipher.
Let’s have quick revisions from previous sessions.
Revision from previous sessions
- Major traditional cipher techniques
- Caesar traditional cipher – type A
- Caesar traditional cipher – type B
- Vigenere Cipher
Recommended Readings:
Cryptography: Basic Understanding
Understanding major cryptographic attacks
Understanding some traditional cipher techniques
Now let’s begin today’s sessions on Block Ciphers
How Digital data processed in Modern Symmetric Key Encryption?
A stream of binary data consists of a long stream of bits (formatted in 0 and 1). Digital data processed in converting one binary stream into another.
What are the methods of Modern Symmetric Key Encryption?
Digital data conversion (as explained above) takes place using two methods, namely:
- Block Cipher
- Stream Cipher (Subset of block ciphers)
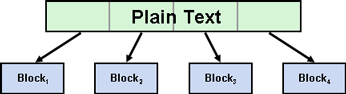
Block Cipher
Block cipher which generates a block of plaintext into a block of cipher text by considering a block of plaintext. The size of cipher text generated is same as the size of plaintext; hence no memory loss has drawn by doing this.
How to determine block size?
It is very important to determine block size as it acts as a determining factor for efficiency calculation. Let us dwell more into the guidelines of block size:
- Most of the computer system manipulates data in the multiple of 8 bits so it is recommended to set block size in the multiple of 8 bits too.
- An engineer should avoid small sized block size to overcome dictionary attack. If any block has size n then plaintext combination should be 2n. It will confuse attackers to create dictionary of data who takes references from previous block cipher or plaintext.
- Sometimes having a large size of block size makes system bulkier, thus tedious to process. So keep the block in optimum size.
Generally, block size does not come in multiple of 8 bits, so we perform padding in block size to make it efficient to decrypt, but too much padding is also not a good practice.
Major Block Cipher’s Schemes
- Digital Encryption Standard (DES)
- Advanced Encryption Standard (AES)
- Triple DES
- Twofish
- IDEA
- Serpent
Feistel Block Cipher
This cipher is the core of all the block ciphers. It allows a cryptographic system to use the same algorithm for encryption and decryption of the data. Digital Encryption Standard (DES) is one the major example of Feistel Block Cipher.
Encryption processes in Feistel Block Cipher
Its encryption process goes through various rounds of plaintext’s processing, followed by substitution and permutation.
Input block in encryption process divided into two half namely left half and right half. Here processes at the right half remain unchanged and left half gets changes as the introduction of encryption keys takes place. Further, key combines with an encryption function and proceeds further on XOR input from left side block and result of the encryption function. Here encryption functions are written as f(Right side block, Key).
Since Feistel cipher goes through various rounds of encryption processes, hence, instead of the key we can derive sub-key at various rounds.
During permutation, constant data of right side gets swiped with variable data of left side. Eventually, the real cipher text is the concatenated data of final right and left results.
Decryption processes in Feistel Block Cipher
We have already discussed that Feistel block cipher uses the same algorithm for encryption as well as decryption. So during description cipher text will be at the place of plaintext and further division will take place in left and right half, followed by substitution and permutation.
Here one important thing to be noted. Sub-keys will be used in reverse order.
How many rounds should we use?
A number of rounds are directly proportional to the highly secure system. So if you increase the number of rounds then the more secure cryptographic system will come out. However, encryption and decryption processing will be slower. Ultimately it depends on the capacity & tradeoff of the system in adopting more number of rounds.